Recently I bought an MTS MBlaze 3G Plus Wi-Fi USB Modem. I picked it because it got pretty good tariff plans & speed compared to other providers in my area. The interesting thing is that it allowed up to 5 devices to connect to it via Wi-Fi. So it appears to me as a fast, cheap, and portable broadband alternative. This device is manufactured by ZTE, a Chinese multinational telecommunications equipment, and systems company.
MBlaze has two way of operation:-
- Connect to Computer and use it like any other USB Net setter.
- Connect to a 5V charger and it will start a Wi-Fi network with connectivity up to 5 devices.
- As I am a Security Guy, I checked the Router web interface of the device and was surprised to see a hell lot of vulnerabilities in a new Device.
- One thing I noticed is that Wi-Fi WPA/WPA2/WEP Key is shown as plain text in the text box.
MTS MBlaze Wi-Fi Password
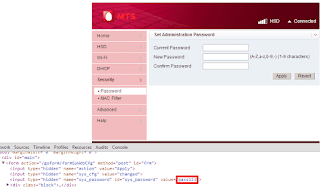
- After some digging outs, it was found that the passwords are hard coded in the source code.
- The router web interface password is hard coded in the password reset page.
MTS MBlaze Router Credentials
- The worst thing was that the session maintaining cookie used by the router web interface is static. This Cookie (iusername=logined) is all you need to get an authenticated session.
- As this session cookie is constant all the time, simply setting the cookie will give access to protected pages in the web interface.
- Another issue I found was, that you can reset the router web interface password without knowing the old password. You don’t even need the session cookie for password resetting.
- The following request is a PoC to reset the password without knowing the old password and with an unauthenticated session.
- This will be considered under OWASP Top 10- A4, Insecure Direct Object Reference.
POST /goform/formSyWebCfg HTTP/1.1 Host: 192.168.1.1 Content-Type: application/x-www-form-urlencoded Referer: https://192.168.1.1/en/password.asp Accept-Encoding: gzip,deflate,sdch Accept-Language: en-US,en;q=0.8,es;q=0.6,ms;q=0.4 Content-Length: 52 action=Apply&sys_cfg=changed&sys_password=newpass |
- Most of the forms in the Router web interface lacks CSRF tokens which essentially make them vulnerable to Cross-Site Request Forgery.
- Putting it all together, I made a quick dirty python POC exploit for MTS MBlaze Ultra Wi-Fi / ZTE AC3633 that can do the following things.
- Bypass Login
- Extract IP Address, Subnet, Gateway Information
- Steal Router Credentials
- Steal Wi-Fi WPA/WPA2/WEP Key
- Reset Password without old password and valid session
- List out the CSRF affected pages
Attack Scenario:-
- Initially, attacker will exploit CSRF and make the victim to visit a page containing the following IFRAME
<iframe src="https://192.168.1.1/goform/formSyWebCfg?wl_encryption_ protocol=3&wl_ wpa_psk_mode=0&wl_wpa_psk_key=xboz&wl_auth_mode=0&oem_cfg=changed& action=Apply" width="0" height="0"> |
- Now the Wi-Fi Key is changed to xboz. From this point, the attacker can connect to the Wi-Fi network and execute the exploit to gain access to the MTS device.
You May Like More:-
- Bsnl Evdo ZTE AC8700 Unlocking Solution Here
- Universal Master Code Calculator to Generate All Zte Modems Unlocking Codes
- Unlock ZTE N799D By Miracle CDMA Boss 1.3
- Unlock ZTE MF29 Usb Modem (Guide) Free
- Unlock Telstra ZTE MF668A 3G USB Modem Totally Free
- Unlock Telstra ZTE MF821 3G USB Modem Totally Free
- Unlock ZTE MF626 MTS RU Modem Totally Free via Firmware Upgrade Process
- Unlock to ZTE AC2746 old ver / AC2766 / AC8720 Modems Free
- How to Find and Get Huawei and Zte 3G Usb Modems Imei Number
- Apn Settings for Mobile Internet USB Modem Dashboard




Hi,
ReplyDeleteHow can I unlock ZTE AC3633 modem?
Thanks and regards,
Debashis
hi sir i am from west bengal i am mts user please tell me about your MTS Mblaze Prepaid Data Plans and also provide details of good offers.
ReplyDelete